If using Microsoft Defender for Office 365 (MDO) as a Security Analyst and want to mitigate stuff (eg. add a domain to the Tenant Level Allow/Block list) you have an issue with the current role model Microsoft provides.
Introduction
Microsoft provides for their Defender products dedicated roles (starting with the least privileged role):
Security Reader: Intended for users to be able to read all security relevant data in Defender 365. Detailed role description: https://learn.microsoft.com/en-us/azure/active-directory/roles/permissions-reference#security-readerSecurity Operator: The designated role for a typical security analyst. This role allows to handle incidents in the Defender 365 console. Detailed role description: https://learn.microsoft.com/en-us/azure/active-directory/roles/permissions-reference#security-operatorSecurity Administrator: With this role all security relevant settings can be done. Detailed role description: https://learn.microsoft.com/en-us/azure/active-directory/roles/permissions-reference#security-administrator
The Issue
If you now assign the role Security Operator to your Analyst you think everything is fine and your Analyst can do what ever is needed in a case of an incident.
In the Microsoft Defender for Office 365 a typical use case could be that your Analyst has to add a specific URL to the Tenant Level Allow/Block list - but this is not possible!
The Root Cause
The root cause is that the Tenant Level Allow/Block list lives in the Exchange Online Tenant and there is a synchronization process in place which synces role assignment from your Entra ID Tenant to the Exchange Online Tenant.
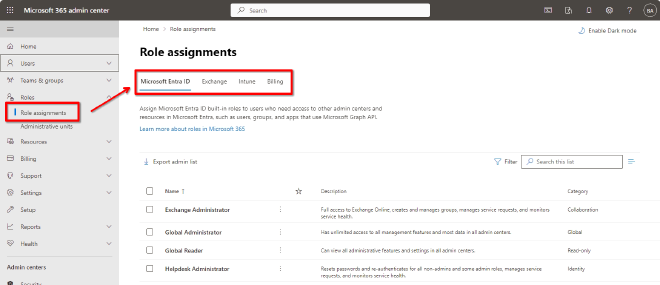
Interestingly only the Entra ID roles Security Reader and Security Administrator are synced. The synced roles in the Exchange Online Tenant can be identified with a unique number after the role name, eg. SecurityReaders_510270795 and SecurityAdmins_-805099513. This role can’t be edited in the Exchange Admin Portal - due they are synced they are read only.
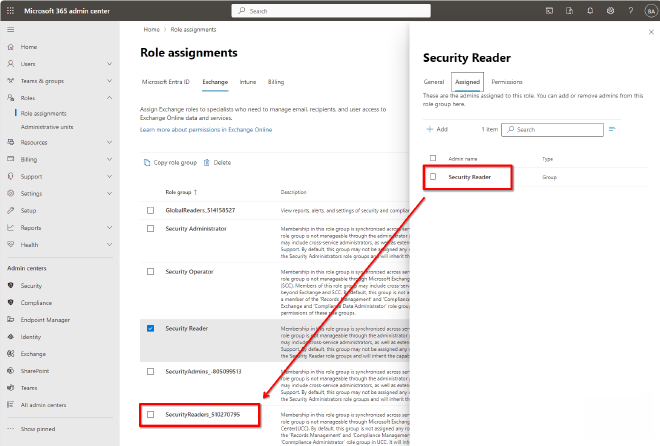
Security Reader with assigned Security Reader role from Entra ID. Unfortunatly it is not directly visible that the name Security Reader in this context points to SecurityReaders_510270795.
As you also can see in the screenshot above is that the role Security Operator with an appended unique number does not exist - ergo does not get synced from Entra ID to Exchange.
The solution
The solution is easy. You have to make sure that your Analysts have the role Security Operator of Exchange assigned or the permission Tenant AllowBlockList Manager. The easiest approach is to go to the Exchange roles and assign the users there the role.
Important to know is the fact that Entra ID securiy groups are not available for the assignment. Thus leads to a management issue - typically you won’t assign the required role in Exchange for each of your Analyst. It would be easier to have a role in Entra ID assigned and automagically you will get the needed role (and permission) in Exchange.
To achieve this my approach is to assing the permission Tenant AllowBlockList Manager to the Exchange role Security Reader. Finally you have just to make sure that your Analysts have assigned the role Security Reader in Entra ID. Et voilà your Analysts are able to configure the Tenant Level Allow/Block list.
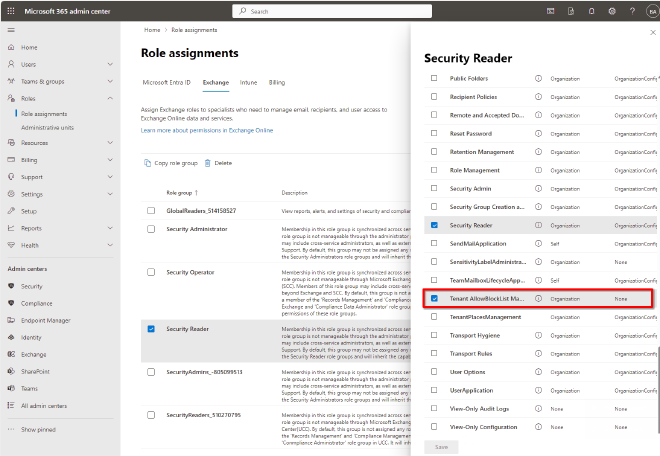
Security Reader with assigned permission Tenant AllowBlockList Manager.
Trap ahead
If you think you could assing the Entra ID role Security Reader to the Exchange role Security Operator - nice try but won’t work.
Drawback
Of course now the predefined role Security Reader has more power in the context of Exchange. Probably there is someone out there which have a nicer solution?
Further Reading
Here are some links: