Oracle is a nice cloud provider which provides some resources for free. That’s perfect if you want to experiment with some web services. But unfortunatly accessing them is not an easy task if you are a beginner in this environment. I will show you what you have to do to get access to your VM (beside of SSH).
Introduction
For testing purposes I was looking for a free tier of Cloud services and found an offer from Oracle Cloud. Details available here: https://www.oracle.com/cloud/free/
Just register and you are ready to go. Creating a VM with an Oracle based image is super easy - I used Ubuntu 22.04. Then I installed a simple web service listening on port 80 and - surprise surprise - the service is not accessible from the internet 🤬.
Examine the issue
After some initial checks like is a service listening on desired port with ss -tlnp I assumed that Oracle has hardened the images with a firewall in place.
root@plnx-srv01:/home/ubuntu# ss -tlnp
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 128 [::]:22 [::]:* users:(("sshd",pid=663,fd=4))
First hurdle
In Linux iptables is used for that job. To see if there are rules in place you just issue following command to save existing rules in a file:
root@plnx-srv01:/home/ubuntu# iptables-save > iptables-rules.txt
And guess - Yes, there where rules. By default Oracle is dropping mostly everything except SSH traffic. So I added an additional rule for my Web service which is listening on port 80. You have to edit file /etc/iptables/rules.v4 (gets automatically applied during boot):
# CLOUD_IMG: This file was created/modified by the Cloud Image build process
# iptables configuration for Oracle Cloud Infrastructure
# See the Oracle-Provided Images section in the Oracle Cloud Infrastructure
# documentation for security impact of modifying or removing these rule
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [463:49013]
:InstanceServices - [0:0]
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p udp --sport 123 -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
# My Custom Rule(s) - START
-A INPUT -p tcp -m state --state NEW -m tcp --dport 80 -j ACCEPT
# My Custom Rule(s) - END
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
-A OUTPUT -d 169.254.0.0/16 -j InstanceServices
-A InstanceServices -d 169.254.0.2/32 -p tcp -m owner --uid-owner 0 -m tcp --dport 3260 -m comment --comment "See the Oracle-Provided Images section in the Oracle Cloud Infrastructure documentation for security impact of modifying or removing this rule" -j ACCEPT
... (other rules left out for better readability)
COMMIT
Second hurdle
After a reboot the firewall rules are in place but still no connection to my web service was possible. I had to do a deeper troubleshooting session with tcpdump (has to be installed). With that tool I found out that no traffic reaches my VM (except SSH).
As many Cloud provider also Oracle provides Network Access Policies to VMs. They are called Ingress Rules and are defined on the Virtual cloud networks of the VM. There you have to add corresponding rules and only if they are defined traffic gets forwarded to your VM.
Navigate to this list by following this steps:
- Go to
Instances - Click on your VM, eg.
instance-20230221-2132 - Click in the “Instance information” view on your subnet, eg.
subnet-20230221-2138 - Now you see your “Security Lists”. Click on it, eg.
Default Security List for vcn-20230221-2138
Finally you just have to add an new ingress rule by hitting on button Add Ingress Rules:
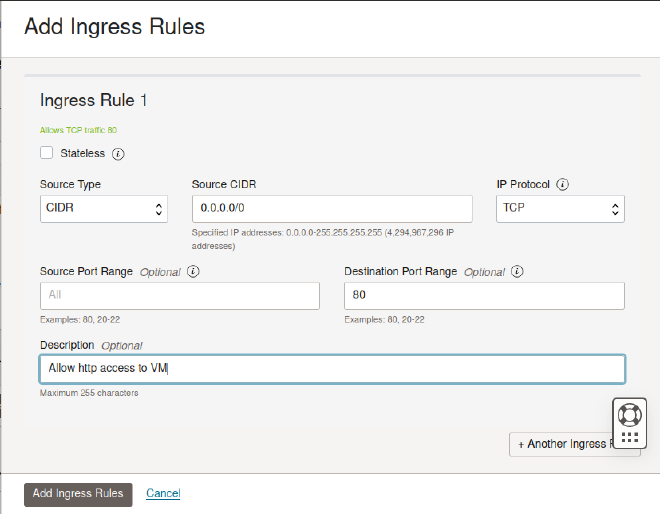
As you can see the rule defines that the whole internet (0.0.0.0/0) is allowed to access port 80 by TCP.
80, 443 in the field Destination Port Range and the GUI will create two dedicated rules, one for port 80 and one for port 443.
After adding this rule you should see it in the list:
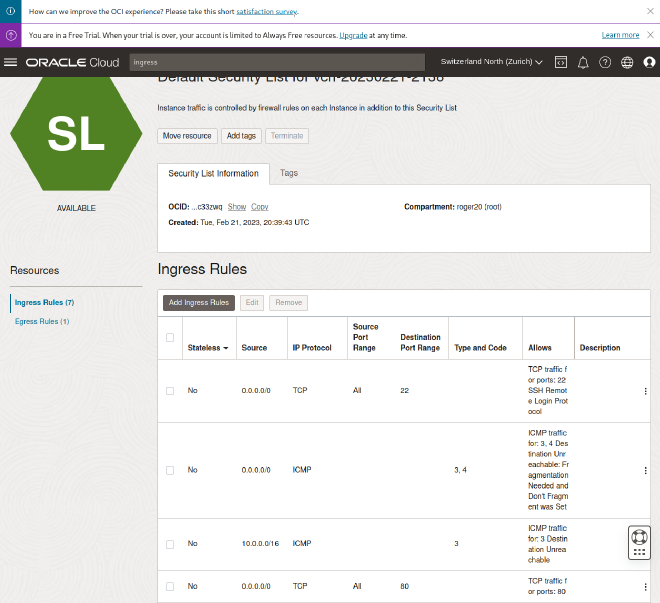
Finally communication from the internet to your VM on port 80/tcp is now working!
Solution
To summarize here is the solution in two simple steps:
- Add firewall rule to local
iptablesdefinition in/etc/iptables/rules.v4 - Edit Ingress Rules for your VM
Now you should have connectivity! 🎉