In the first part of this serie we checked the basics of the Graph API. Now in this part we will use Logic App to query the API. This opens new way to automate tasks.
Introduction
In the last article of this series we saw how to query Graph API with PowerShell. NAn alternative way to query Graph API is to use Logic App. This article is not an introduction into Logic App but could be helpful to start using Graph API with Logic App.
Compared to the post Graph API with PowerShell
we will query the API for all users with their userPrincipalName.
As we learned we can use Graph Explorer to find out which Graph API URI we have to call to achieve this goal: https://graph.microsoft.com/v1.0/users?$select=userPrincipalName
Implementation
Implementation looks straight forward. In this example I used Occurence as the starting point of the Logic App. For accessing Graph API we use the block type HTTP and fill in the required information:
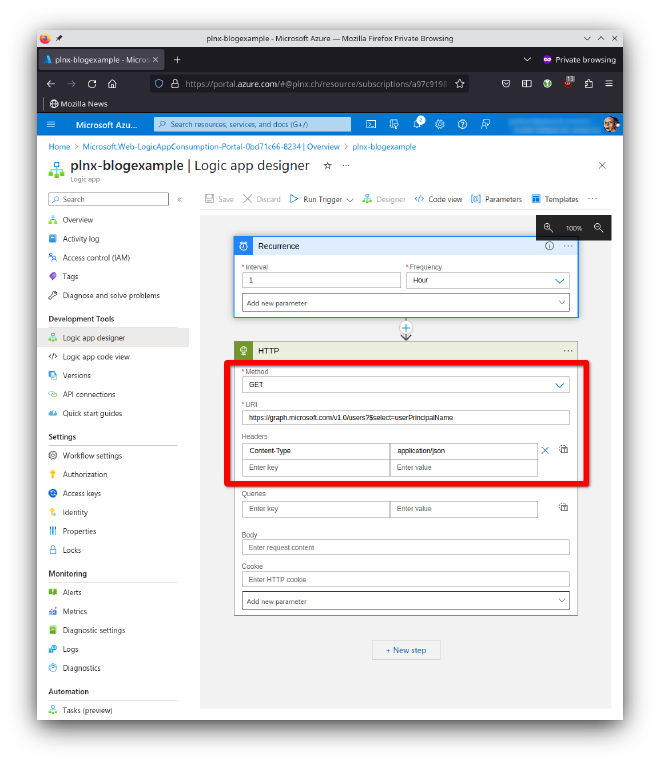
To test your Logic App hit now on Run Trigger → Run. The result will be s
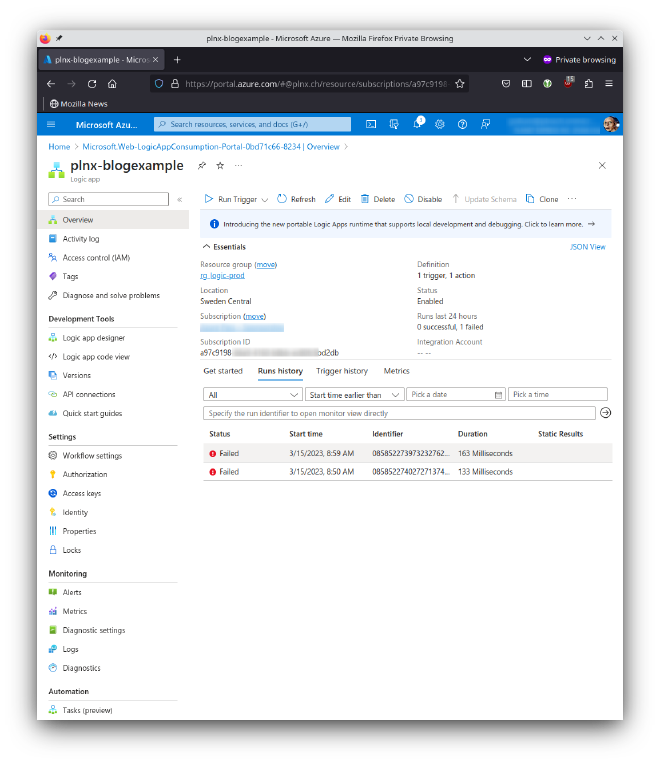
To discover the reason why the run failed hit on the message and open the flow:
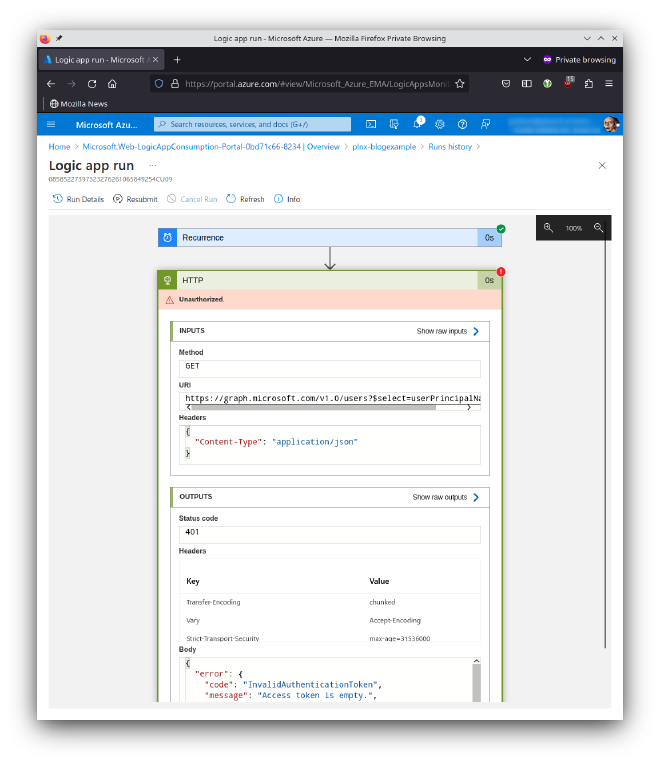
The issue: Unauthorized
As clearly stated in the screenshot the Logic App is not authorized to use the Graph API. All requests to Graph API have to be done with corresponding access token. For this purpose also the Logic App has to be authenticated. From here there are two possibilities:
- Use an App registration
- Use a Managed Identity
App registrations are easy. To learn something new I decided to go the way with Managed Identity. Change to Identity and activate there the System assigned variant of managed identity by setting Status to On and hit Save.
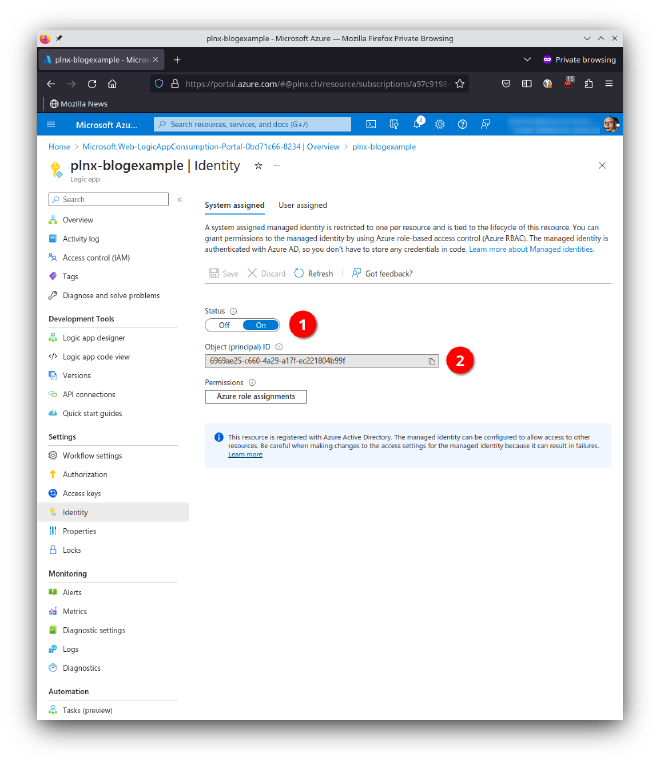
As soon as you save your settings, an object is created in your Azure AD and gets an Object ID (marked as “2”), in our case 6969ae25-c660-4a29-a17f-ec221804b99f.
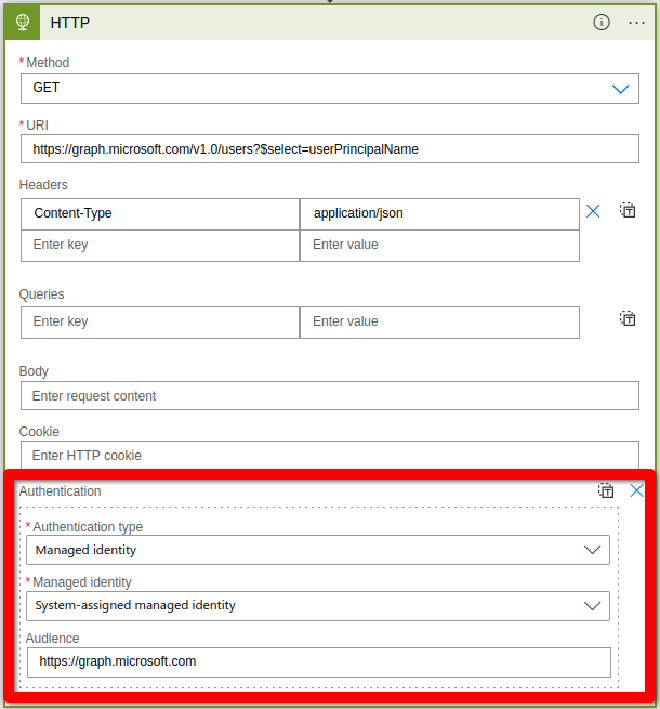
Now we have to change our HTTP block to use this managed identity for authentication. For this you select your HTTP block, check Authentication and you get additional fields you can fill in:
- Authentication type: Managed Identity
- Managed Identity: System-assigned managed identity
- Audience: https://graph.microsoft.com
Now let’s try again our Logic App to see if it is working now. Unfortunatly it does not. You will get something similar to this:
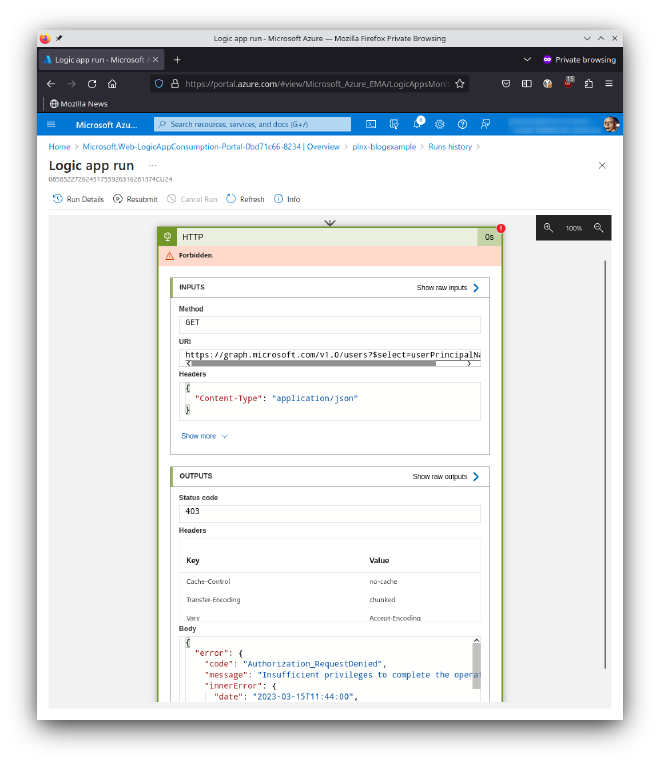
The 2nd issue: Forbidden
Now we are a step closer to our desired goal to fetch data from the Graph API. As it looks like we are able to authenticate but still not able to fetch data from the API. If you think about it is clear: You need permission on the API to use it - or in this scenario the managed identity needs the right permissions. We want to assign the permission Directory.Read.All to the managed identity. When this is done we should be able to query the Graph API.
Unfortunatly there is no GUI to assign appropriate permissions to the managed identity. For this you have to use some PowerShell magic.
Connect-MgGraph -Scopes 'Application.ReadWrite.All,AppRoleAssignment.ReadWrite.All'
$graph = Get-MgServicePrincipal -Filter "AppId eq '00000003-0000-0000-c000-000000000000'"
$permission = $graph.AppRoles `
| where Value -Like "Directory.Read.All" `
| Select-Object -First 1
$msi = Get-MgServicePrincipal -Filter "Id eq '6969ae25-c660-4a29-a17f-ec221804b99f'"
New-MgServicePrincipalAppRoleAssignment `
-ServicePrincipalId $msi.Id `
-AppRoleId $permission.Id `
-PrincipalId $msi.Id `
-ResourceId $graph.Id
Final result
After all if you hit now Run on the Logic App you will see that the workflow completes without an error:
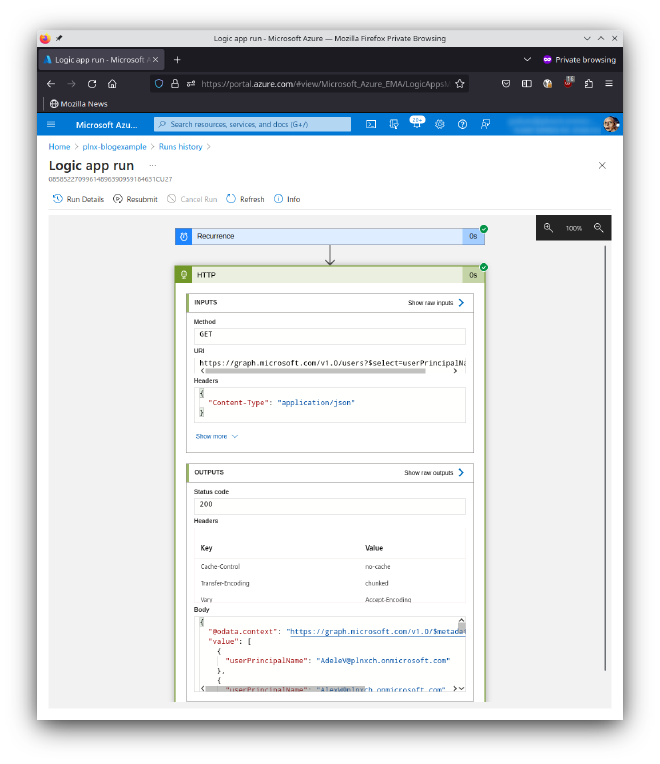
Of course this workflow does not make sense. It just shows how to connect to the Graph API to fetch data from a Logic App. This are the key take aways:
- Create Logic App
- Create Managed Identity (System Assigned)
- Grant API permission to Managed Identity with PowerShell
- Use HTTP block to access Graph API with proper settings for authentication incl. audience part
Further Reading
As usual there are many resources available if you are interested to learn more about Logic App. Here are some links:
- Walkthrough creating a Logic App: https://learn.microsoft.com/en-us/azure/logic-apps/quickstart-create-first-logic-app-workflow