In another post I already wrote about managed identities and using API. There I also showed how to adapt the required permissions. In this post you will see how to set up required permissions for Microsoft Defender for Endpoint (internally called WindowsDefenderATP).
Introduction
In the post about Graph API with Logic App I already showed how to use Managed Identity and assign required permissions to it.
Unfortunatly if you want to use Microsoft Defender for Endpoint API it is not as easy as described in the mentioned post. The biggest challenge is to find out which permissions you could assign to your managed identity.
Implementation
What you need to know is the magic Id of the application to get the permissions out of it (meaning that you can use the PowerShell script you find in the mentioned post above).
The magic Id for WindowsDefenderATP (the internal name of Microsoft Defender for Endpoint) is: fc780465-2017-40d4-a0c5-307022471b92.
For our example we want to assign the following permissions to the managed identity:
Alert.ReadWrite.AllMachine.ReadWrite.AllMachine.Isolate
Here is the corresponding PowerShell script:
$managedIdentityId = '8396e306-d3d0-4b6f-8b47-f73dfbeecadf'
$myPermissions = "Alert.ReadWrite.All", "Machine.ReadWrite.All", "Machine.Isolate"
Connect-MgGraph -Scopes 'Application.ReadWrite.All,AppRoleAssignment.ReadWrite.All'
$msi = Get-MgServicePrincipal -Filter "Id eq '$managedIdentityId'"
$mde = Get-MgServicePrincipal -Filter "AppId eq 'fc780465-2017-40d4-a0c5-307022471b92'"
foreach ($myPerm in $myPermissions) {
$permission = $mde.AppRoles `
| where Value -Like $myPerm `
| Select-Object -First 1
if ($permission) {
New-MgServicePrincipalAppRoleAssignment `
-ServicePrincipalId $msi.Id `
-AppRoleId $permission.Id `
-PrincipalId $msi.Id `
-ResourceId $mde.Id
}
}
Disconnect-MgGraph
To verify what you have done you could use following command:
Get-MgServicePrincipalAppRoleAssignment -ServicePrincipalId $msi.Id | fl
Logic App Workflow
Now here an example Logic App workflow which will use the managed identity to operate on the Defender for Endpoint API:
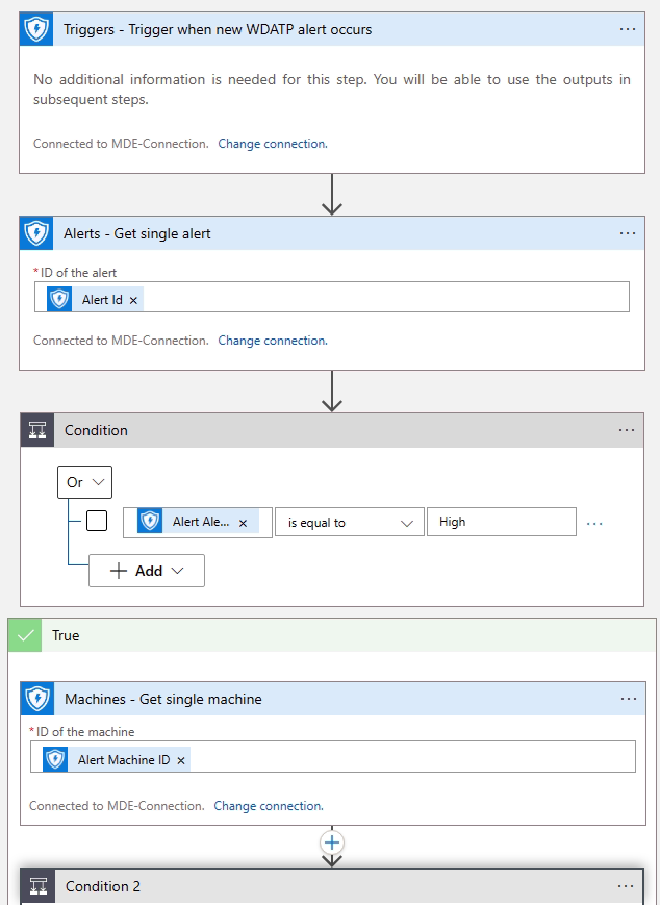
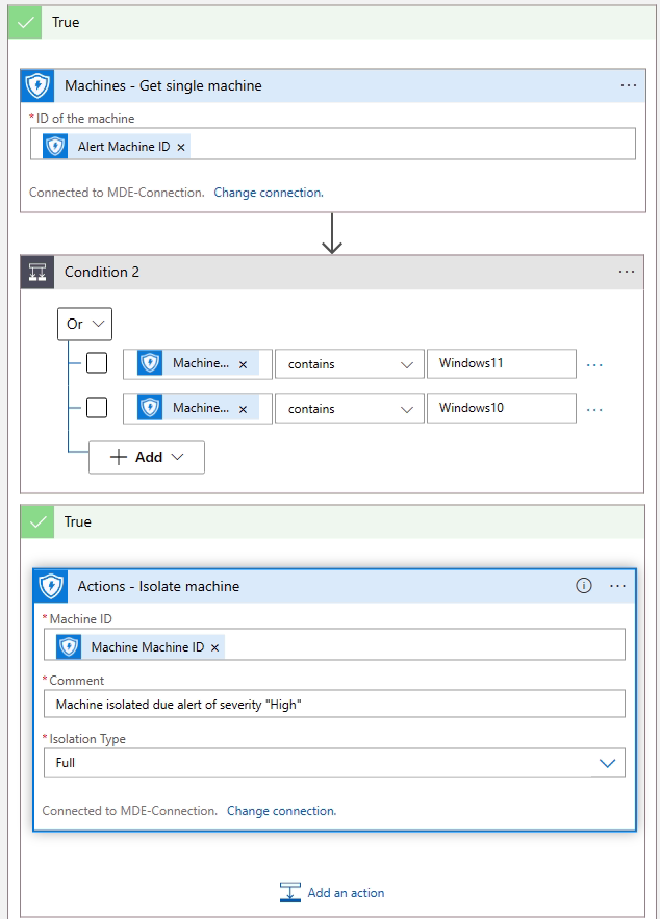
Windows10 or Windows11 isolate system.
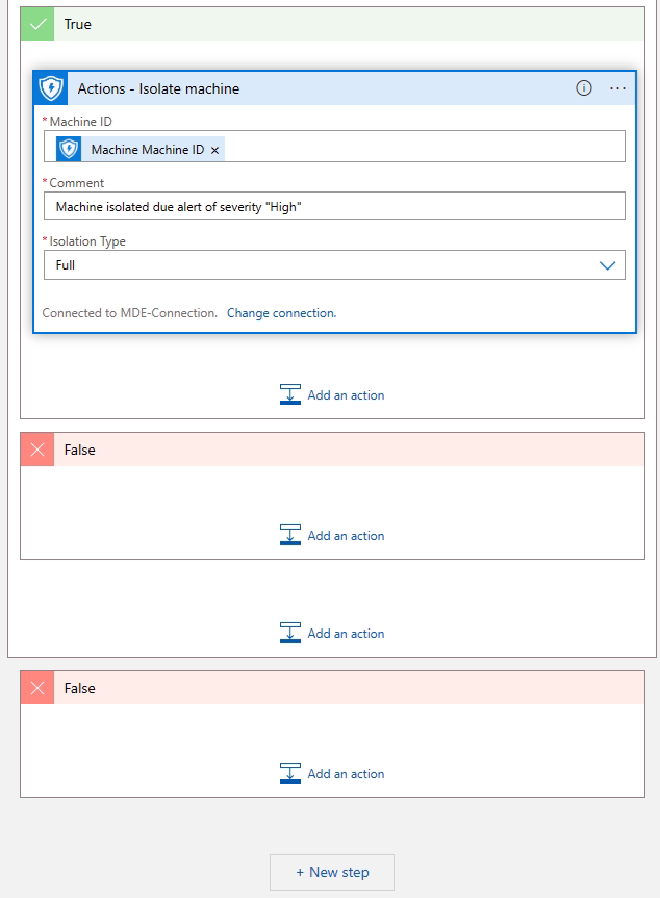
Final result
Of course this workflow does not make sense. It just shows how to connect to the Graph API to fetch data from a Logic App. This are the key take aways:
- Create Logic App
- Create Managed Identity (System Assigned)
- Grant API permission to Managed Identity with PowerShell
- Use WDATP block to access Microsoft Defender for Endpoint API
Further Reading
Here are some links: